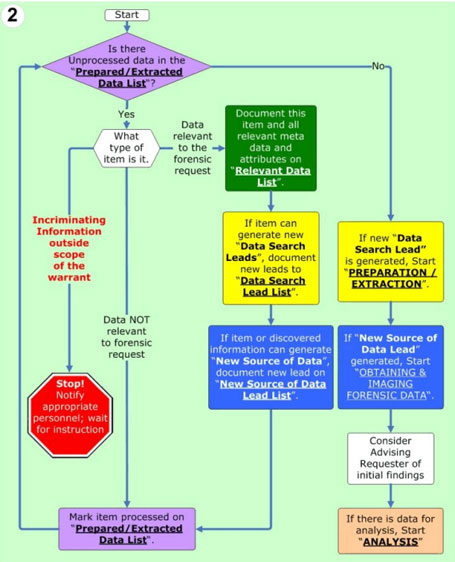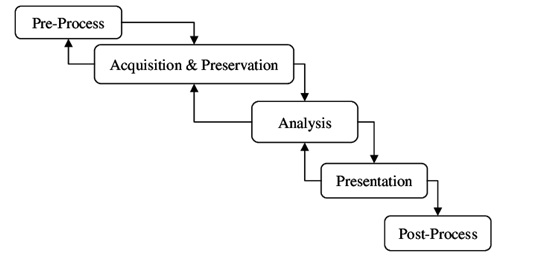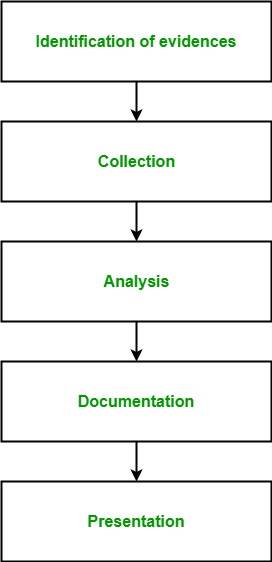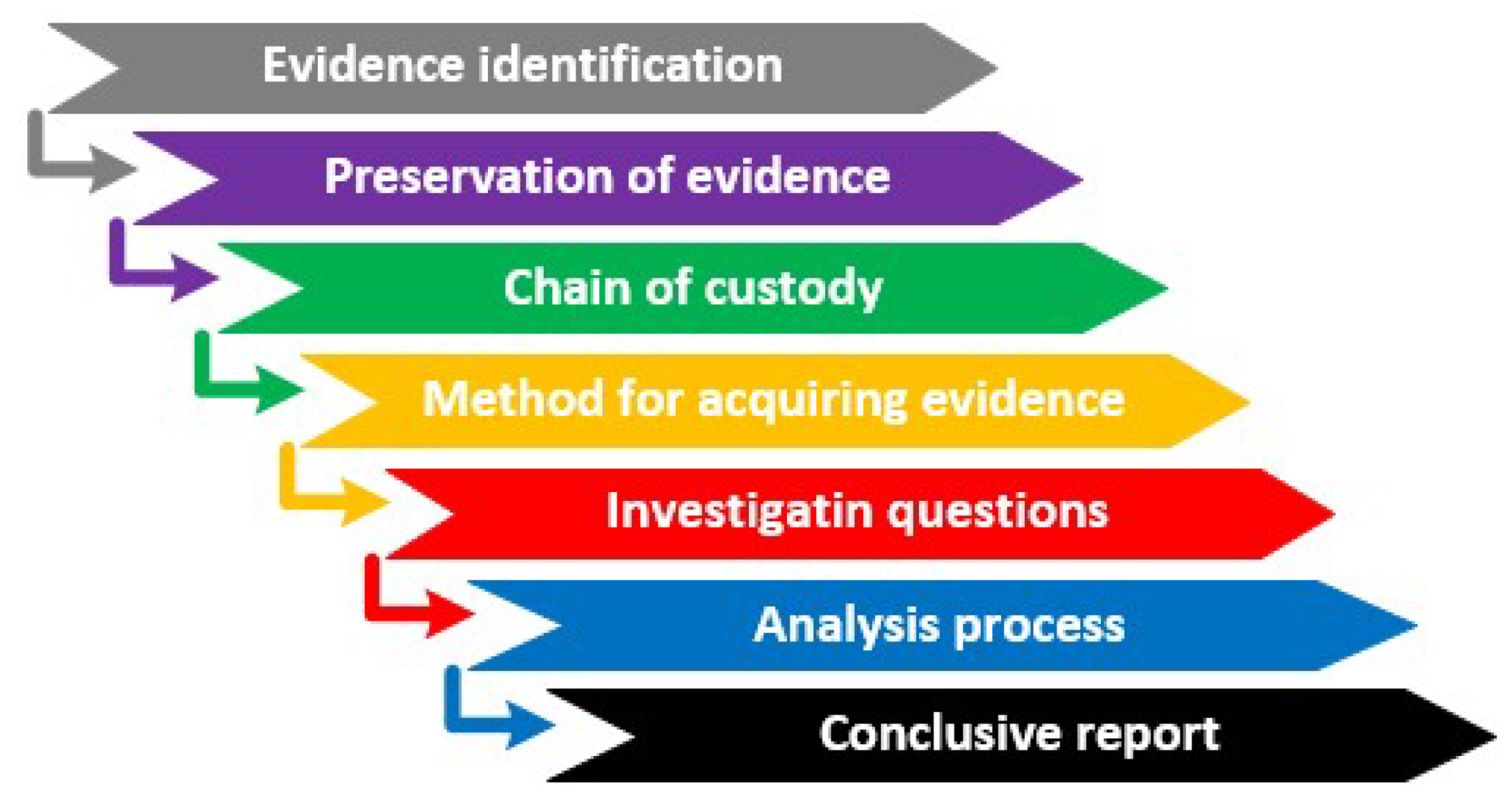
Applied Sciences | Free Full-Text | Methodology for Forensics Data Reconstruction on Mobile Devices with Android Operating System Applying In-System Programming and Combination Firmware

Fundamentals of Digital Forensics: Theory, Methods, and Real-Life Applications : Kävrestad, Joakim: Amazon.in: Books
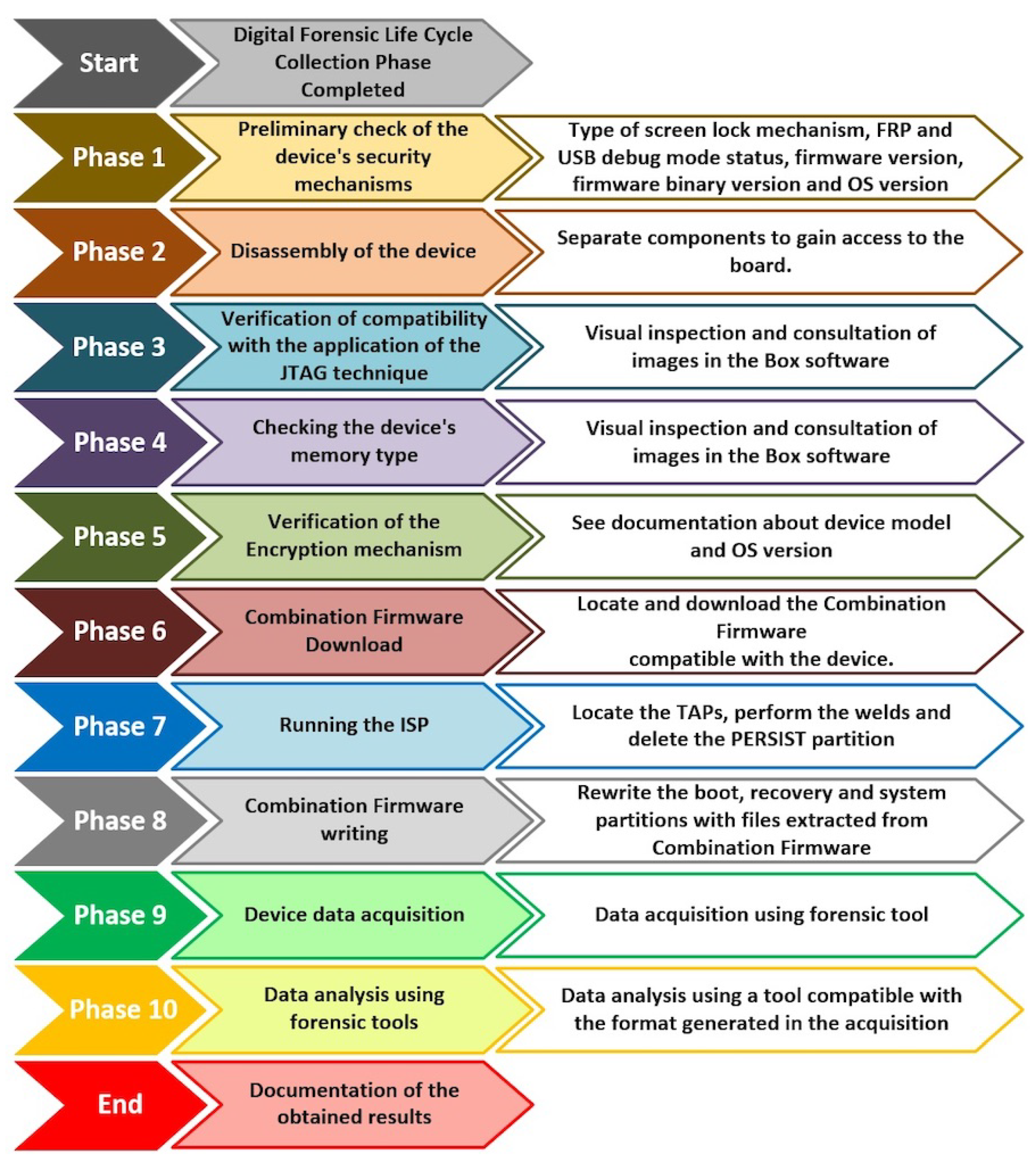
Applied Sciences | Free Full-Text | Methodology for Forensics Data Reconstruction on Mobile Devices with Android Operating System Applying In-System Programming and Combination Firmware



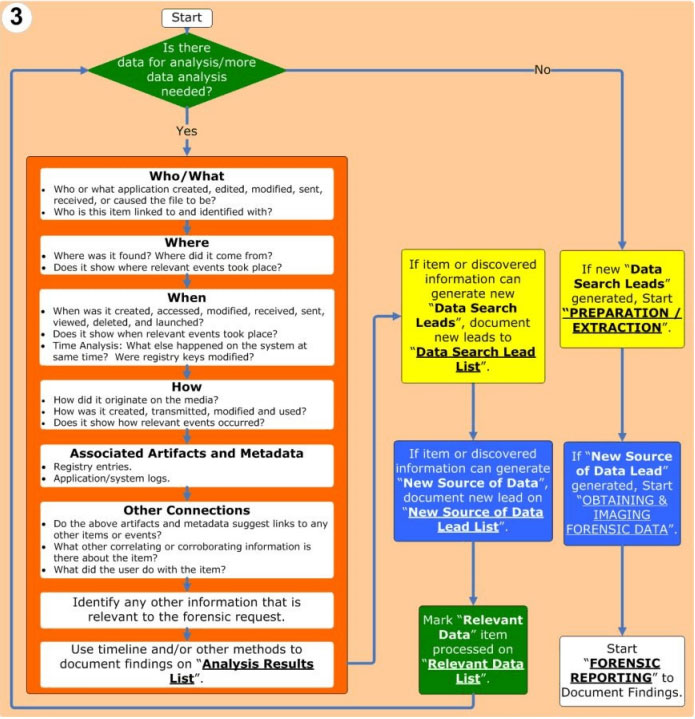

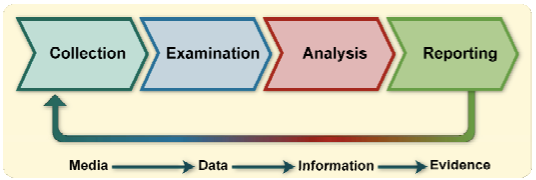
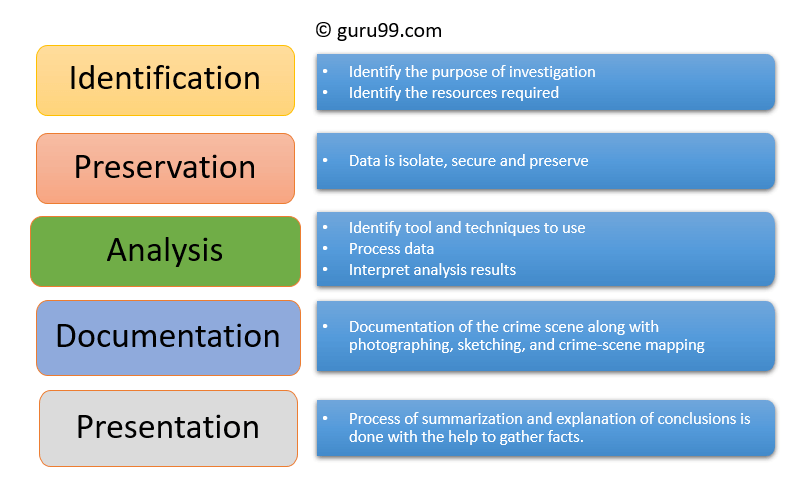




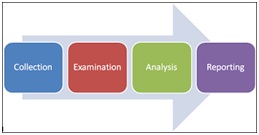




.png)