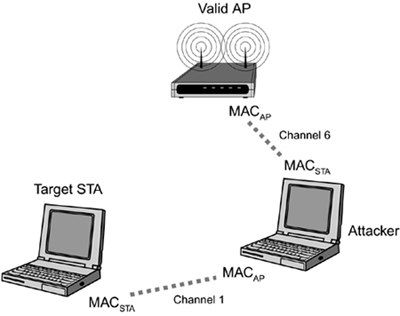
Man-in-the-Middle Attacks :: Chapter 15. Known Attacks: Technical Review :: Part III: Wi-Fi Security in the Real World :: 802.11 security. wi-fi protected access and 802.11i :: Networking :: eTutorials.org

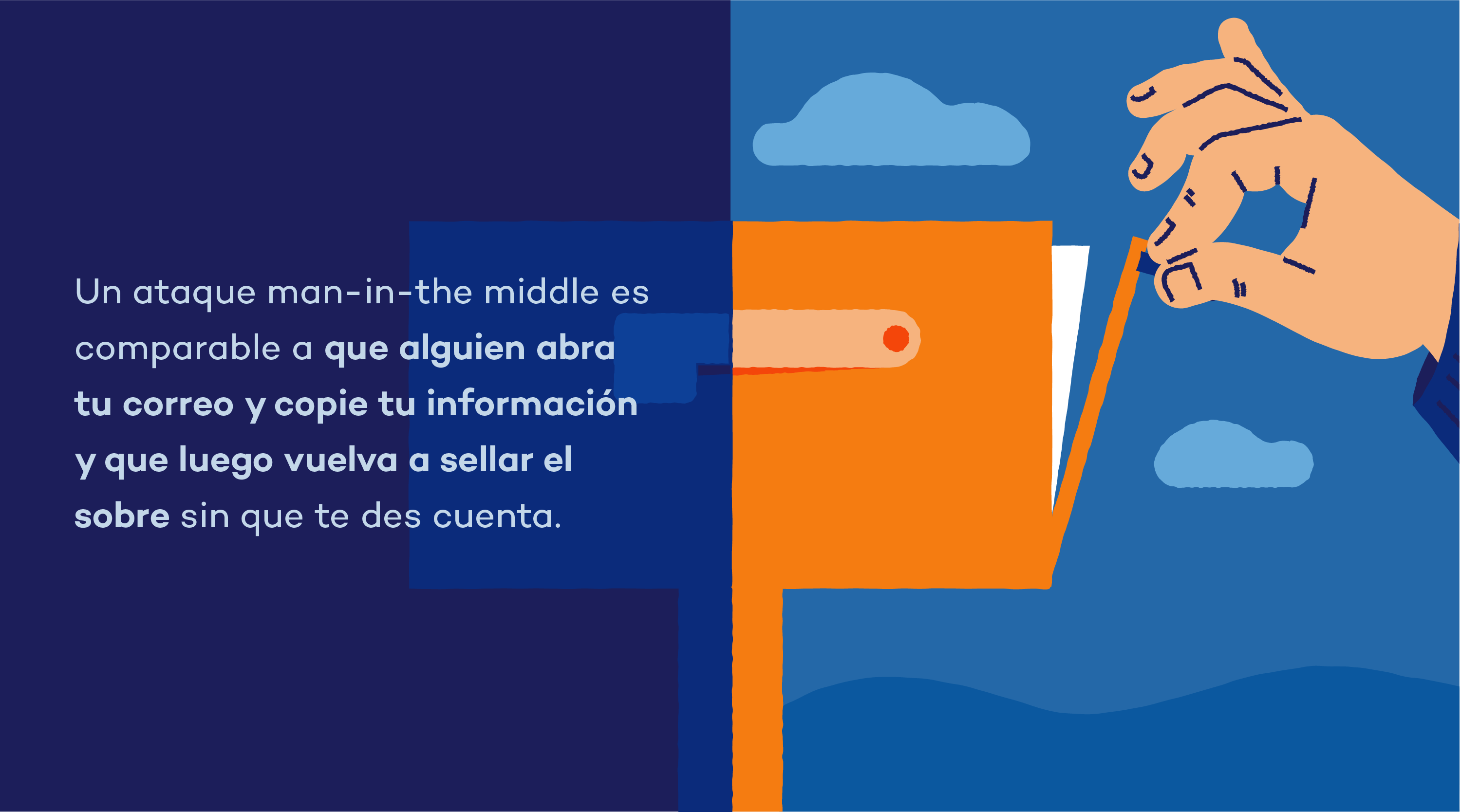
Infosec Guide: Defending Against Man-in-the-Middle Attacks - Новости о безопасности - Trend Micro RU
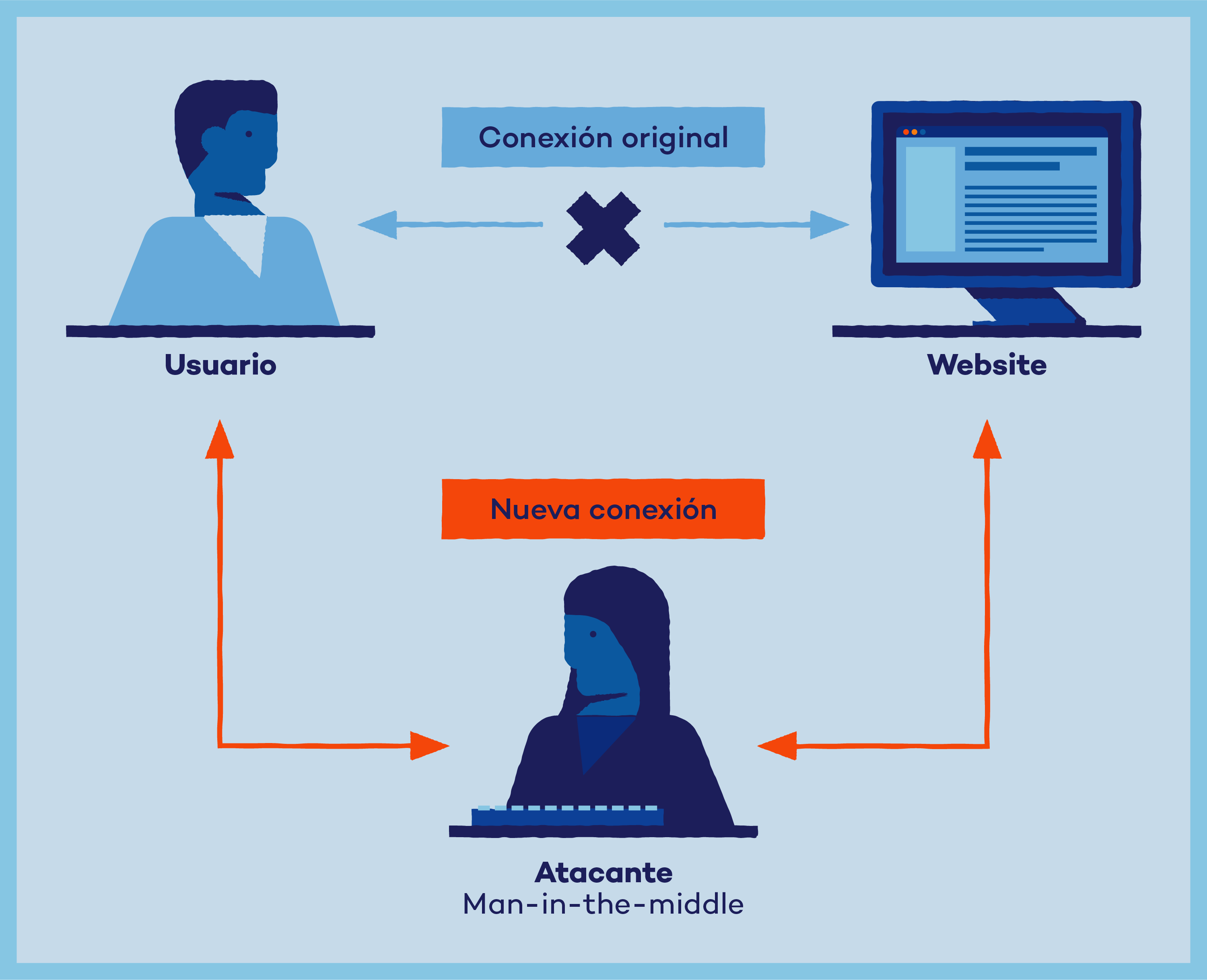
![Basic Hacking] Understanding the Man In the middle Attack - Networking - 0x00sec - The Home of the Hacker Basic Hacking] Understanding the Man In the middle Attack - Networking - 0x00sec - The Home of the Hacker](https://0x00sec.org/uploads/default/original/1X/4e9fa2371e722b44723f65988dd1a1280566b0f8.png)

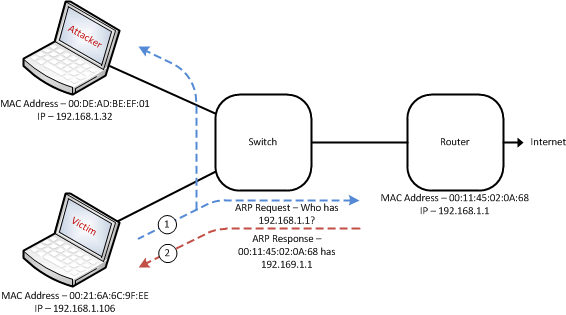


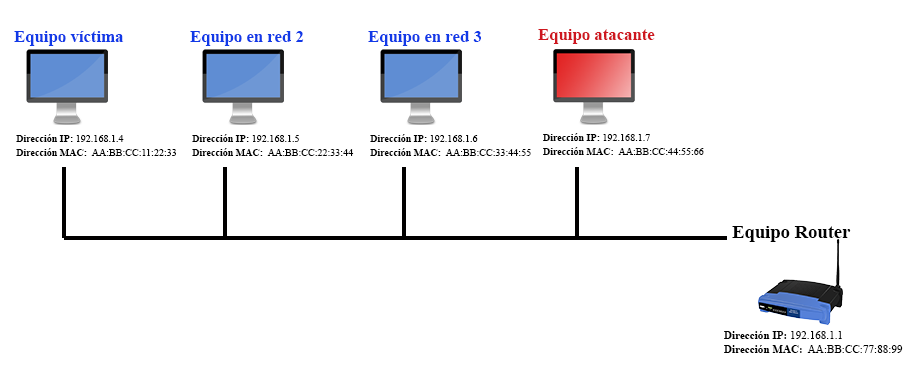





![PDF] Man-in-the-Middle Attack to the HTTPS Protocol | Semantic Scholar PDF] Man-in-the-Middle Attack to the HTTPS Protocol | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/c9d274536a1411eaee27a54d949d478da7eef16b/2-Figure1-1.png)
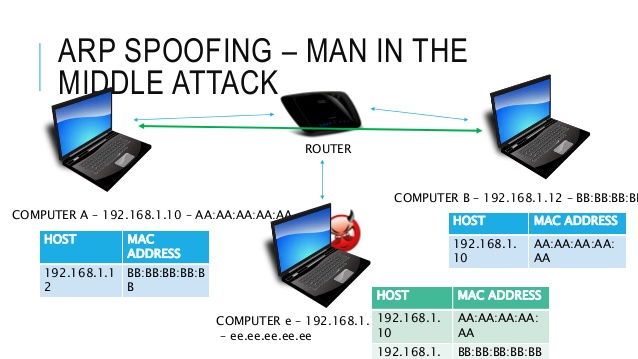
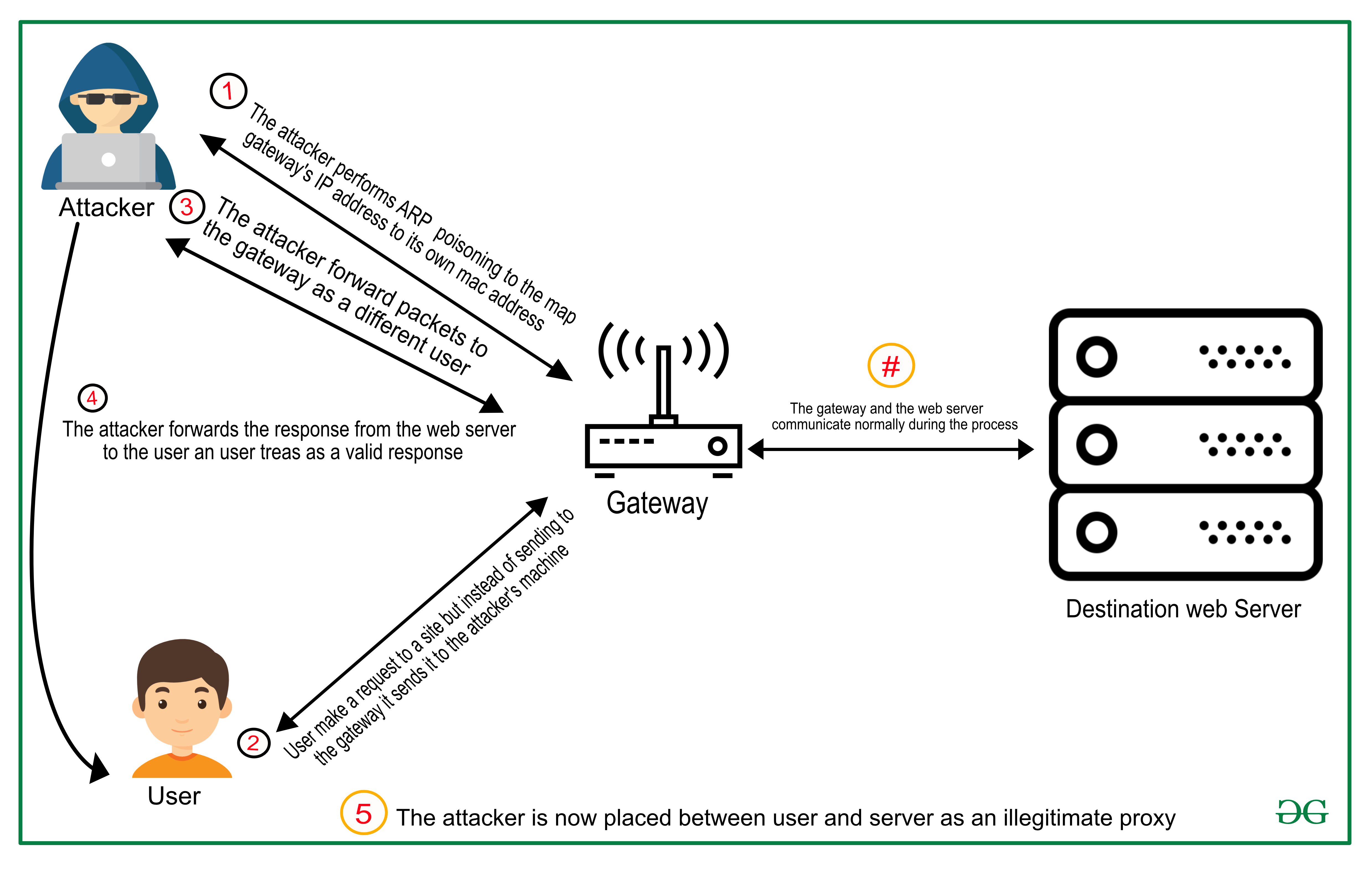

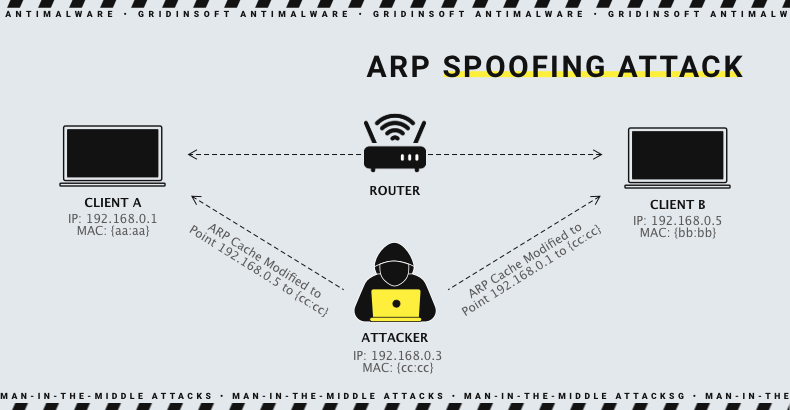




![PDF] Man in the Middle Attack : Prevention in Wireless LAN | Semantic Scholar PDF] Man in the Middle Attack : Prevention in Wireless LAN | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/11cc3ecaf1a077c061e50049982bd385f58083e9/2-Figure1-1.png)

